On va parler de fingerprinting dans ce petit topic de blog. Tout ordinateur qui intéragit dans un réseau tel que internet à une empreinte numérique. Il y a des techniques pour reconnaitre ces caractéristiques.
Cela fait partie des stratégies des hackers pour rechercher des vulnérabilités. On peut découvrir beaucoup d'information sur un site internet via le fingerprinting. C'est la phase RECON en hacking.
Amusons nous sur blog.kor51.org
Tout d'abord, on récupère le fichier d'en-tête du site pour connaitre le type de webserver.
$ curl -I blog.kor51.org
HTTP/1.1 301 Moved Permanently
Server: nginx/1.22.1
Date: Fri, 10 Jan 2025 05:46:29 GMT
Content-Type: text/html
Content-Length: 169
Connection: keep-alive
Location: https://blog.kor51.org/
On a ainsi le webserver, c'est Nginx en version 1.22.1 et généralement on peut commencer à rechercher des vulnérabilités en faisant une requête sur exploit-db.com
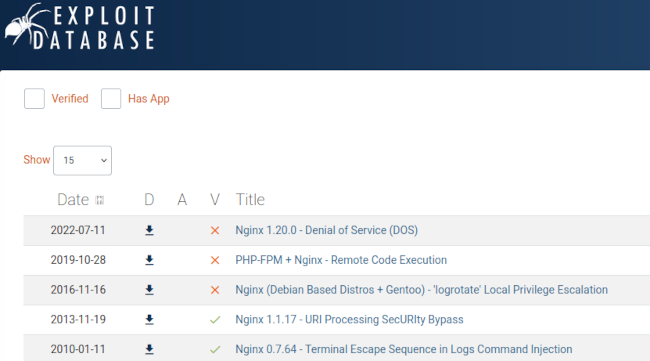
On apprends ainsi que la version 1.20.0 est vulnérable à un DDOS. Cela l'air d'être safe.
On va essayer de trouver le système d'exploitation (OS) à la recherche de vulnérabilité.
$ sudo nmap -O blog.kor51.org
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-10 06:51 CET
Nmap scan report for blog.kor51.org (82.64.210.252)
Host is up (0.0070s latency).
rDNS record for 82.64.210.252: 82-64-210-252.subs.proxad.net
Not shown: 961 closed tcp ports (reset), 37 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
443/tcp open https
Device type: general purpose|router
Running (JUST GUESSING): Linux 5.X|4.X|2.6.X|3.X (90%), MikroTik RouterOS 7.X (90%)
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3 cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
Aggressive OS guesses: Linux 5.0 - 5.14 (90%), MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3) (90%), Linux 4.19 - 5.15 (89%), Linux 4.15 - 5.19 (86%), OpenWrt 21.02 (Linux 5.4) (86%), Linux 2.6.32 - 3.13 (85%), Linux 5.1 - 5.15 (85%), OpenWrt 22.03 (Linux 5.10) (85%)
No exact OS matches for host (test conditions non-ideal).
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.39 seconds
Ainsi on a moins de chance, nmap ne détecte pas l'OS. Il sait que c'est du Linux, mais ne trouve pas la version exacte.
On va tenter un DNS Enumeration et rechercher l'IP du serveur:
$ dig blog.kor51.org
; <<>> DiG 9.20.3 <<>> blog.kor51.org
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 7654
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;blog.kor51.org. IN A
;; ANSWER SECTION:
blog.kor51.org. 2210 IN A 82.64.210.252
Le serveur est surement protégé via DNSSEC contre l'enumeration car il ne trouve pas l'autre site kor51.org. On a une IP de serveur. Dans le A record.
On va rechercher le fournisseur du nom de domaine en faisant une requête:
$ whois kor51.org
Domain Name: kor51.org
Registry Domain ID: 76e57416d1074ff582e309ba996eec41-LROR
Registrar WHOIS Server: http://whois.ovh.com
Registrar URL: http://www.ovh.com
Updated Date: 2024-10-21T17:38:51Z
Creation Date: 2023-09-06T17:38:06Z
Registry Expiry Date: 2025-09-06T17:38:06Z
Registrar: OVH sas
Registrar IANA ID: 433
Registrar Abuse Contact Email: abuse@ovh.net
Registrar Abuse Contact Phone: +33.972101007
Domain Status: clientDeleteProhibited https://icann.org/epp#clientDeleteProhibited
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Registry Registrant ID: REDACTED FOR PRIVACY
Registrant Name: REDACTED FOR PRIVACY
Registrant Organization:
Registrant Street: REDACTED FOR PRIVACY
Registrant City: REDACTED FOR PRIVACY
Registrant State/Province:
Registrant Postal Code: REDACTED FOR PRIVACY
Registrant Country: FR
Registrant Phone: REDACTED FOR PRIVACY
Registrant Phone Ext: REDACTED FOR PRIVACY
Registrant Fax: REDACTED FOR PRIVACY
Registrant Fax Ext: REDACTED FOR PRIVACY
Registrant Email: Please query the RDDS service of the Registrar of Record identified in this output for information on how to contact the Registrant, Admin, or Tech contact of the queried domain name.
Registry Admin ID: REDACTED FOR PRIVACY
Admin Name: REDACTED FOR PRIVACY
Admin Organization: REDACTED FOR PRIVACY
Admin Street: REDACTED FOR PRIVACY
Admin City: REDACTED FOR PRIVACY
Admin State/Province: REDACTED FOR PRIVACY
Admin Postal Code: REDACTED FOR PRIVACY
Admin Country: REDACTED FOR PRIVACY
Admin Phone: REDACTED FOR PRIVACY
Admin Phone Ext: REDACTED FOR PRIVACY
Admin Fax: REDACTED FOR PRIVACY
Admin Fax Ext: REDACTED FOR PRIVACY
Admin Email: Please query the RDDS service of the Registrar of Record identified in this output for information on how to contact the Registrant, Admin, or Tech contact of the queried domain name.
Registry Tech ID: REDACTED FOR PRIVACY
Tech Name: REDACTED FOR PRIVACY
Tech Organization: REDACTED FOR PRIVACY
Tech Street: REDACTED FOR PRIVACY
Tech City: REDACTED FOR PRIVACY
Tech State/Province: REDACTED FOR PRIVACY
Tech Postal Code: REDACTED FOR PRIVACY
Tech Country: REDACTED FOR PRIVACY
Tech Phone: REDACTED FOR PRIVACY
Tech Phone Ext: REDACTED FOR PRIVACY
Tech Fax: REDACTED FOR PRIVACY
Tech Fax Ext: REDACTED FOR PRIVACY
Tech Email: Please query the RDDS service of the Registrar of Record identified in this output for information on how to contact the Registrant, Admin, or Tech contact of the queried domain name.
Name Server: dns107.ovh.net
Name Server: ns107.ovh.net
DNSSEC: signedDelegation
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
>>> Last update of WHOIS database: 2025-01-10T06:26:05Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
Terms of Use: Access to Public Interest Registry WHOIS information is provided to assist persons in determining the contents of a domain name registration record in the Public Interest Registry registry database. The data in this record is provided by Public Interest Registry for informational purposes only, and Public Interest Registry does not guarantee its accuracy. This service is intended only for query-based access. You agree that you will use this data only for lawful purposes and that, under no circumstances will you use this data to (a) allow, enable, or otherwise support the transmission by e-mail, telephone, or facsimile of mass unsolicited, commercial advertising or solicitations to entities other than the data recipient's own existing customers; or (b) enable high volume, automated, electronic processes that send queries or data to the systems of Registry Operator, a Registrar, or Identity Digital except as reasonably necessary to register domain names or modify existing registrations. All rights reserved. Public Interest Registry reserves the right to modify these terms at any time. By submitting this query, you agree to abide by this policy. The Registrar of Record identified in this output may have an RDDS service that can be queried for additional information on how to contact the Registrant, Admin, or Tech contact of the queried domain name.
Il nous a trouver: OVH.
On peut même trouver le FAI du serveur:
$ whois 82.64.210.252
% This is the RIPE Database query service.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See https://docs.db.ripe.net/terms-conditions.html
% Note: this output has been filtered.
% To receive output for a database update, use the "-B" flag.
% Information related to '82.64.0.0 - 82.67.255.255'
% Abuse contact for '82.64.0.0 - 82.67.255.255' is 'abuse@proxad.net'
inetnum: 82.64.0.0 - 82.67.255.255
netname: FR-PROXAD-20030403
country: FR
org: ORG-PISP1-RIPE
admin-c: ACP23-RIPE
tech-c: TCP8-RIPE
status: ALLOCATED PA
mnt-by: RIPE-NCC-HM-MNT
mnt-by: PROXAD-MNT
mnt-routes: PROXAD-MNT
created: 2003-04-03T09:27:48Z
last-modified: 2018-02-14T01:51:58Z
source: RIPE # Filtered
organisation: ORG-PISP1-RIPE
org-name: Free SAS
country: FR
org-type: LIR
address: 16 rue de la Ville l'Eveque
address: 75008
address: Paris
address: FRANCE
phone: +33173502000
fax-no: +33173922555
admin-c: ACP23-RIPE
admin-c: TCP8-RIPE
mnt-ref: PROXAD-MNT
mnt-ref: RIPE-NCC-HM-MNT
mnt-by: RIPE-NCC-HM-MNT
mnt-by: PROXAD-MNT
tech-c: TCP8-RIPE
remarks: Pour les requisitions judiciaires/administratives, merci de contacter par fax le 33 1 73 92 25 55
abuse-c: ACP23-RIPE
created: 2004-04-17T11:23:24Z
last-modified: 2020-12-16T12:45:25Z
source: RIPE # Filtered
role: Administrative Contact for ProXad
address: Free SAS / ProXad
address: 8, rue de la Ville L'Eveque
address: 75008 Paris
phone: +33 1 73 50 20 00
fax-no: +33 1 73 92 25 69
remarks: trouble: Information: http://www.proxad.net/
remarks: trouble: Spam/Abuse requests: mailto:abuse@proxad.net
admin-c: APfP1-RIPE
tech-c: TPfP1-RIPE
nic-hdl: ACP23-RIPE
mnt-by: PROXAD-MNT
abuse-mailbox: abuse@proxad.net
created: 2002-06-26T12:46:56Z
last-modified: 2013-08-01T12:16:00Z
source: RIPE # Filtered
role: Technical Contact for ProXad
address: Free SAS / ProXad
address: 8, rue de la Ville L'Eveque
address: 75008 Paris
phone: +33 1 73 50 20 00
fax-no: +33 1 73 92 25 69
remarks: trouble: Information: http://www.proxad.net/
remarks: trouble: Spam/Abuse requests: mailto:abuse@proxad.net
admin-c: APfP1-RIPE
tech-c: TPfP1-RIPE
nic-hdl: TCP8-RIPE
mnt-by: PROXAD-MNT
created: 2002-06-26T12:29:10Z
last-modified: 2011-06-14T09:03:07Z
source: RIPE # Filtered
abuse-mailbox: abuse@proxad.net
% Information related to '82.64.0.0/14AS12322'
route: 82.64.0.0/14
descr: ProXad network / Free SA
descr: Paris, France
origin: AS12322
mnt-by: PROXAD-MNT
created: 2003-04-03T09:35:03Z
last-modified: 2003-04-03T09:35:03Z
source: RIPE # Filtered
% This query was served by the RIPE Database Query Service version 1.114 (SHETLAND)
Il a également trouver le FAI: Free
Enfin on peut rechercher les technologies derrière un website, tel que le framework et connaitre sa stack server. Ainsi c'est généralement plus simple de hacker des sites sous Wordpress. Ce qui donne pour ce blog via l'extension Wappalyzer
- Generateur de site statique: Pelican
- Script de police: Fonts Awesome
- Librairie Javascript: JQuery 1.7.2
- Framework UI: Boostrap
- Divers: Pygments
- Langage de programmation: Python